I’ve been running Pi-hole with DNS-Over-HTTPS using Cloudflare’s DoH client (cloudflared) for some time now; I followed the guide posted here on the official Pi-hole documentation site. When updating the cloudflared recently, I noticed it displayed some errors when the service tried to start up. After digging around, I found that cloudflared now has an option to install itself as a service whereas the guide I used includes steps for creating the service manually. Thus, I believe this is a simpler way to setup cloudflared as your DNS-Over-HTTPS client for Pi-hole.
Download the cloudflared daemon and install it:
|
1 2 |
wget https://bin.equinox.io/c/VdrWdbjqyF/cloudflared-stable-linux-amd64.deb sudo apt install ./cloudflared-stable-linux-amd64.deb |
Create a folder and config file for the cloudflared daemon:
|
1 2 3 4 5 6 7 8 |
sudo mkdir /etc/cloudflared sudo vi /etc/cloudflared/config.yml proxy-dns: true proxy-dns-port: 5053 proxy-dns-upstream: - https://1.1.1.1/dns-query - https://1.0.0.1/dns-query |
Use the following command to instruct cloudflared to install itself as service:
|
1 |
sudo cloudflared service install |
Start the new cloudflared service and check the status:
|
1 2 |
sudo service cloudflared start sudo service cloudflared status |
You should get output similar to the following if successful:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
● cloudflared.service - Argo Tunnel Loaded: loaded (/etc/systemd/system/cloudflared.service; enabled; vendor preset: enabled) Active: active (running) since Mon 2019-09-02 03:50:20 UTC; 1s ago Main PID: 1479 (cloudflared) Tasks: 7 (limit: 4661) CGroup: /system.slice/cloudflared.service └─1479 /usr/local/bin/cloudflared --config /etc/cloudflared/config.yml --origincert /etc/cloudflared/cert.pem --no-autoupdate Sep 02 03:50:20 sandbox systemd[1]: Starting Argo Tunnel... Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="Version 2019.8.4" Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="GOOS: linux, GOVersion: go1.12.7, GoArch: amd64" Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg=Flags config=/etc/cloudflared/config.yml no-autoupdate=true origincert=/et Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="Adding DNS upstream" url="https://1.1.1.1/dns-query" Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="Adding DNS upstream" url="https://1.0.0.1/dns-query" Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="Starting DNS over HTTPS proxy server" addr="dns://localhost:5053" Sep 02 03:50:20 sandbox cloudflared[1479]: time="2019-09-02T03:50:20Z" level=info msg="Starting metrics server" addr="127.0.0.1:39507" Sep 02 03:50:20 sandbox systemd[1]: Started Argo Tunnel. |
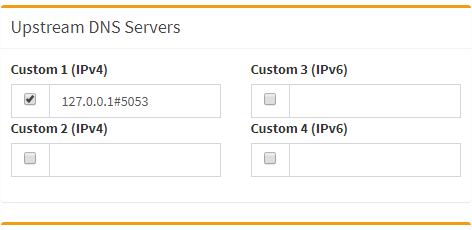
Now just configure Pi-hole to use cloudflared as the DNS resolver: